Hackers Listen to Your Passwords!
A group of researchers hailing from British universities has undertaken a pioneering project in the realm of cybersecurity: a way hackers can LISTEN to your passwords. This involves the development of a sophisticated deep learning model with the capability to extract sound data from keyboard keystrokes recorded utilizing a microphone, achieving an astonishing accuracy rate of 95%. The significance of this achievement stems from its potential to compromise computer data security on an unprecedented scale.
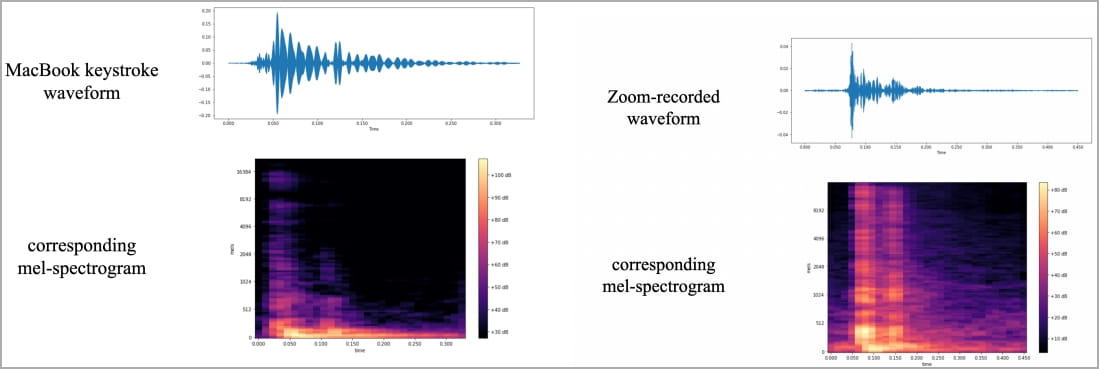
Interestingly, when the researchers employed Zoom for training the sound classification algorithm, the prediction accuracy experienced a marginal dip, settling at a still disconcerting 93%. This achievement itself marked a groundbreaking record in the domain of medium-specific attacks, raising concerns about the implications for data protection.
The implications of such an attack are profound, jeopardizing the sanctity of individuals' data by potentially exposing their passwords, conversations, messages, and other confidential information to malicious third parties. Unlike several other side-channel attacks that necessitate specific conditions and are bound by limitations related to data rates and distances, acoustic-based attacks have acquired a new level of simplicity due to the ubiquity of microphone-equipped devices capable of executing high-fidelity audio captures. This convergence of factors—ranging from the proliferation of recording-enabled devices to the rapid strides taken in the realm of machine learning—has elevated sound-based side-channel attacks from a theoretical concept to a genuinely potent and unexpectedly perilous threat.
The process of executing such an attack revolves around the act of capturing keystrokes on the target's keyboard, which is crucial for training the prediction algorithm. This task can be accomplished through a nearby computer microphone or even via the target's smartphone (iPhone or Android or Windows), which might have been compromised by malware granting unauthorized microphone access. Alternatively, keystrokes can be intercepted through a Zoom call where an illegitimate participant leverages message-sound correlations to their advantage.
To generate training data, the researchers embarked on a meticulous exercise: they pressed 36 keys on a contemporary MacBook Pro, repeating this process 25 times per key while simultaneously recording the auditory output of each press. The resultant recordings were transformed into waveforms and spectrograms, the latter serving as visual representations that display discernible distinctions for each individual key. Through meticulous data processing techniques, the researchers augmented the signals to facilitate accurate keystroke identification.
In the quest to harness the power of this data, the researchers introduced 'CoAtNet,' an image classifier specifically trained on the spectrogram images. This project entailed a series of empirical investigations involving varying parameters such as epochs, learning rates, and data partitioning. These systematic trials eventually yielded optimal prediction accuracy outcomes.
In their experimental trials, the researchers adhered to consistent computer hardware setups, relying on a laptop featuring the same keyboard design utilized across Apple laptops for the preceding two years. Additionally, they placed an iPhone 13 mini at a distance of 17 centimetres from the target, and the Zoom platform was leveraged to record audio. Remarkably, the CoAtNet classifier demonstrated its prowess by attaining a staggering 95% accuracy when processing smartphone-recorded audio, and maintaining a still formidable 93% accuracy when dealing with audio gleaned from Zoom calls. Moreover, Skype, another popular communication medium, yielded a slightly lower yet still formidable accuracy rate of 91.7%.
In light of this alarming revelation, the researchers have proposed several potential strategies to counter the looming threat of acoustic side-channel attacks. For individuals plagued by apprehension, the paper recommends exploring alterations to typing styles or the adoption of randomized passwords. Alternative measures encompass the implementation of software designed to replicate keystroke sounds, the introduction of white noise, or the utilization of software-driven keystroke audio filters.
It is worth noting that the efficacy of the attack model endured even when confronted with the presence of exceptionally quiet keyboards. Consequently, the incorporation of sound dampeners on mechanical keyboards or transitioning to membrane-based keyboards is unlikely to provide meaningful protection against such threats.
Ultimately, the researchers advocate for the adoption of biometric authentication where feasible, along with the prudent employment of computer password managers to circumvent the need for manual input of sensitive information. As the cybersecurity landscape evolves in the face of emerging threats, these mitigation tactics stand as critical bulwarks against the potential breaches posed by sound-based side-channel attacks.
Call us if you want information on password managers and how to use them.

